Cyber Apocalypse 2021 CTF has been organized by HackTheBox (19 Apr 2021 – 23 Apr 202) and it was my second CTF overall and the first forensic CTF I have tried. It involved quite a lot of googling and brainstorming with my friend HatsuMora, but I managed to get my first forensic flag!
Resources that helped and inspired me was:
- CTF Series : Forensics
- Decode KeyStrokes from USB-PCAP [For CTF]
- kaizen-ctf 2018 — Reverse Engineer usb keystrok from pcap file
- HID Usage Tables
Walkthrough
In this task, we were provided with a USB-based PCAP file. As there are many USB devices, you have to inspect the packets to figure out which USB devices are connected. The packet you are interested in is called GET DESCRIPTOR Response DEVICE.
When you look in the packets, expand DEVICE DESCRIPTOR and find idVendor and idProduct. From the name, you can figure out what device has been used. In our case, it is the Razer BlackWidow Ultimate 2016 keyboard.
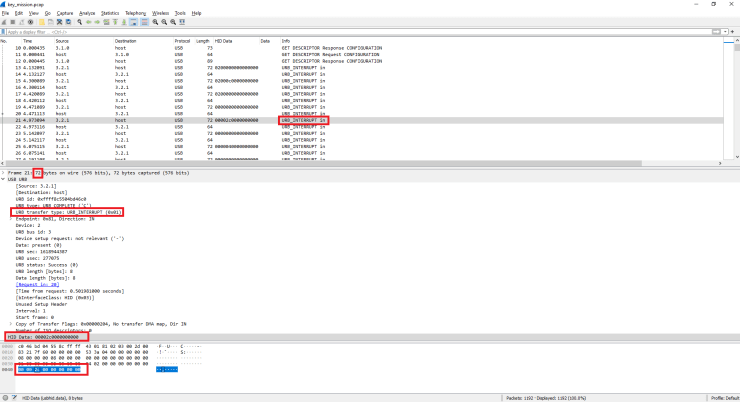
Knowing it has been the keyboard, we can take a look at the interrupt messages.
When you look into the details of different URB_INTERRUPT packages, you can notice some of them have 8 extra bytes added at the end. Those frames are 72 bytes and have the HID Data field (in many sources online, called Leftover Capture Data).
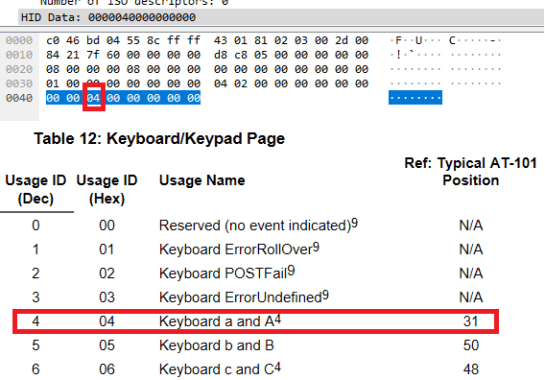
After checking HID Usage Tables we can see that the 3rd byte we see in Wireshark corresponds to a specific key pressed on the keyboard. As you can see in the table, “04” can mean either a or A. So how do you know which one was pressed? The answer to this can be found in the first byte. If it is 02, then the Shift has been pressed, and the letter is a capital letter.
Having that information, we need to gather all the frames with HID data and extract bytes corresponding to keystrokes that have been pressed.
To display the frames we are interested in, we need to apply a filter that will show us only URB_INTERRUPT in that was 72 bytes in size.
((usb.transfer_type == 0x01) && (frame.len == 72))
We want to export the pcap as CSV to run a script that converts the HEX to letters. To do that, we need to add HID DATA to the column (right-click on HID Data in packet details and choose “Apply as a column”) and export packet dissection as a CVS file.
The next step is to extract the HID Data from the file. To do that run the command:
cat keypcap.csv | cut -d "," -f 7 | cut -d "\"" -f 2 | grep -vE "HID Data" > hexoutput.txt
Then we need to run a short python script that decodes the keystrokes. I was inspired by a script I have downloaded from Rajchowdhury420 GitHub.
After running the original script, I have noticed a failure “KeyError: 42”. Checking again in the HID Usage table, I have discovered that 42 (or 2A in hex) means that a “Backspace” button was pressed, resulting in the previous character being deleted.
After adjusting a script, I managed to capture the flag!
The Wireshark and script are available on my GitHub.